Hardware giant GIGABYTE hit by RansomEXX ransomware
[ad_1]
Taiwanese motherboard maker hit by RansomEXX ransomware gang, threatening to release 112GB of stolen data unless ransom is paid
Gigabyte is best known for its motherboards, but also manufactures other computer components and hardware, such as graphics cards, data center servers, laptops and monitors.
The attack happened late overnight Tuesday through Wednesday and forced the company to shut down systems in Taiwan. The incident also affected several of the company’s websites, including its support site and parts of the Taiwanese website.
Customers also reported issues accessing support documents or receiving updated RMA information, which is likely due to the ransomware attack.
According to Chinese news site United Daily News, Gigabyte has confirmed that it suffered a cyberattack that affected a small number of servers.
After detecting abnormal activity on their network, they shut down their computer systems and notified law enforcement.
If you have first-hand information about this or other unreported cyberattacks, you can contact us confidentially on Signal at +16469613731 or Wire at @ lawrenceabrams-bc.
Gigabyte suffers RansomEXX ransomware attack
While Gigabyte has not officially declared which ransomware operation carried out the attack, BleepingComputer has learned that it was carried out by the RansomEXX gang.
When RansomEXX operation encrypts a network, they create ransom notes on every encrypted device.
These ransom notes contain a link to a non-public page intended to be accessible only to the victim to test the decryption of a file and leave an email address to begin ransom negotiations.
Today, a source sent BleepingComputer a link to a non-public RansomEXX leak page for Gigabytes Technologies, where threat actors claim to have stolen 112 GB of data in the attack.
In a ransom note also seen by BleepingComputer, the threat actors state: “Hello, Gigabyte (gigabyte.com)!” and include the same link to the private leak page shared with us by our source.
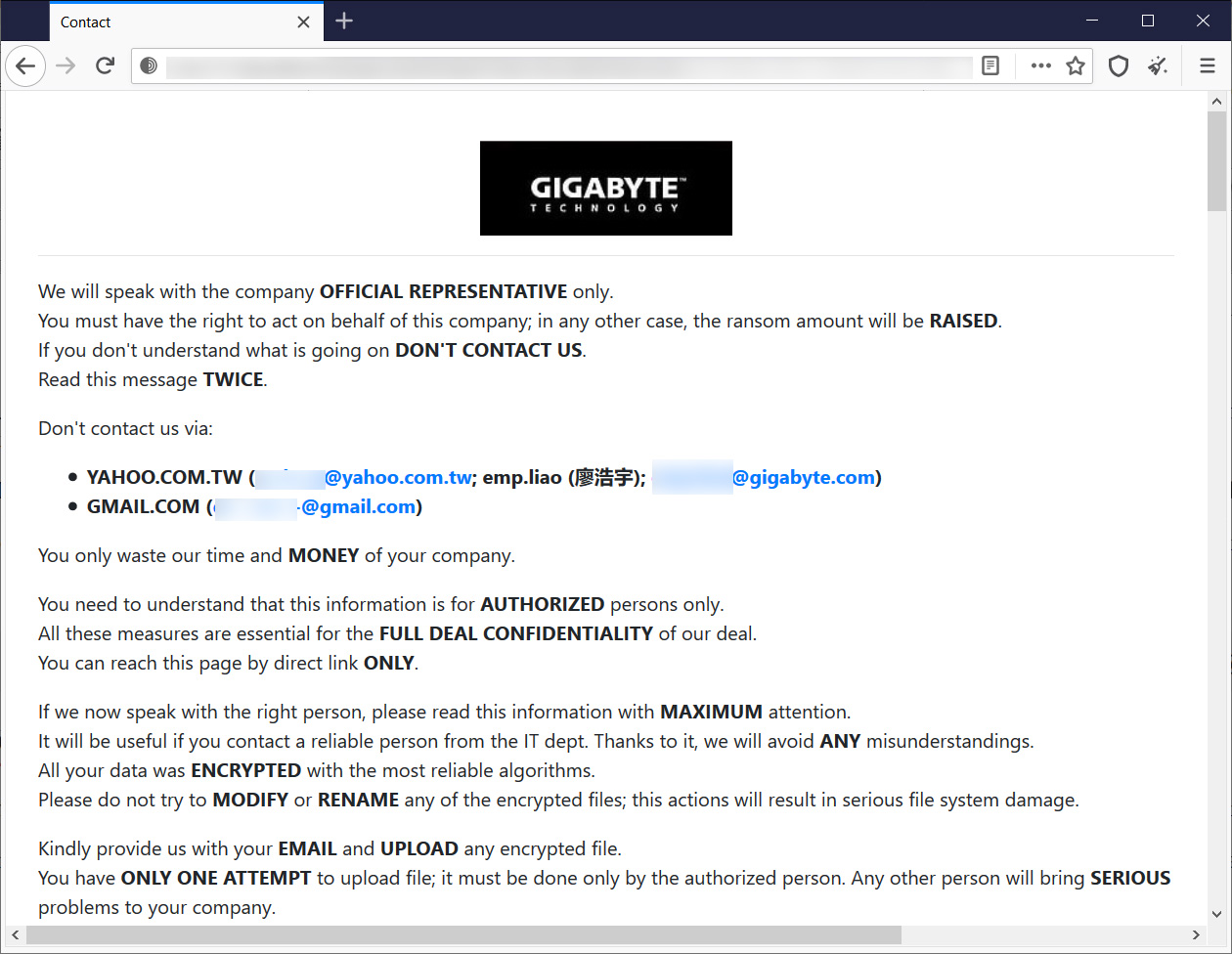
On this non-public leaked page, the threat actors claim to have stolen 112 GB of data from an internal Gigabyte network as well as the US Megatrends Git repository,
We have downloaded 112 GB (120,971,743,713 bytes) of your files and are ready to PUBLISH them.
Many of them are under NDA (Intel, AMD, American Megatrends).
Leak sources: newautobom.gigabyte.intra, git.ami.com.tw and a few others.
On the private data leak page, the threat actors also shared screenshots of four NDA documents stolen in the attack.
While we will not release the leaked images, the confidential documents include a US Megatrends debug document, an Intel “potential issues†document, an “Ice Lake D SKU stack update schedule†and an AMD review guide. .
BleepingComputer attempted to contact Gigabyte regarding the attack but has not received a response yet.
What you should know about RansomEXX
The RansomEXX ransomware operation originally started as Defray in 2018, but was renamed RansomEXX in June 2020 when it became more active.
Like other ransomware operations, RansomEXX will violate a network via Remote Desktop protocol, exploits or stolen credentials.
Once they gain access to the network, they will collect more credentials as they gradually take control of the Windows domain controller. During this lateral spread across the network, the ransomware gang will steal data from unencrypted devices used as leverage in ransom extortions.
RansomEXX not only targets Windows devices, but has also created a Linux encryptor to encrypt virtual machines running VMware ESXi servers.
Over the past month, the RansomEXX gang has become more active as they recently attacked the Italian region of Lazio and the Ecuadorian state-run Corporación Nacional de Telecomunicación (CNT).
Other high-profile attacks by the ransomware gang include Brazilian government networks, the Texas Department of Transportation (TxDOT), Konica Minolta, IPG Photonics, and Tyler Technologies.
[ad_2]

