MoonBounce malware hides in your BIOS chip and persists after drive formatting
A new type of malware takes a decidedly stealthier and harder-to-remove path through your operating system – it hides in your BIOS chip and therefore remains even after you reinstall your operating system or format your hard drive.
Kaspersky has observed the growth of Unified Extensible Firmware Interface (UEFI) malware threats since 2019, with most malware stored on the EFI system partition of the PC storage device. However, a sinister development has been spotted in the new year with new UEFI malware, detected by Kasperksy’s firmware scanner logs, which implants malicious code into the motherboard’s Serial Peripheral Interface (SPI) flash. . Security researchers have dubbed this flash-resident UEFI malware “MoonBounce”.
MoonBounce isn’t the first UEFI malware discovered in the wild that targets SPI flash. Kaspersky says LoJax and MosaicRegressor preceded it. However, MoonBounce shows “significant progress, with a more complicated attack flow and greater technical sophistication”. It also appears to have infected a remote machine.
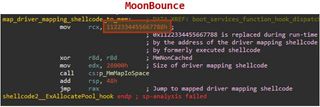
MoonBounce is undeniably smart in the way it enters a system and makes itself difficult to detect and eliminate. “The source of the infection starts with a set of hooks that intercept the execution of several functions in the EFI boot services table,” Kaspersky explains on its SecureList blog. The hooks are then used to divert function calls to the malicious shellcode the attackers added to the CORE_DXE image. This, in turn, “establishes additional hooks in subsequent components of the boot chain, namely the Windows loader,” the security researchers said. This allows malware to be injected into a svchost.exe process when the computer boots into Windows.
Transport Technology Company, the only recorded attack to date
Of course, Kaspersky was interested to see what the malware would do next. Thus, on an infected machine, the researchers observed that the malicious process tried to access a URL to retrieve the payload for the next stage and execute it in memory. Interestingly, this part of the sophisticated attack didn’t seem to go anywhere, so it wasn’t possible to analyze any other stages in MoonBounce. Perhaps this malware was still in the testing phase when it was spotted and/or retained for some particular purpose. Additionally, the malware is not file-based and performs at least some of its operations solely in memory, making it difficult to see exactly what MoonBounce has been doing on a single company network host PC.
A single machine, owned by a shipping company, appears to be the only machine on Kaspersky’s logs that has a MoonBounce infection in its Flash SPI. It is not known exactly how the infection occurred, but it is thought to have been caused remotely. This single machine from a transport technology company appears to have spread non-UEFI malware implants to other machines on the network. With much of his work fileless and resident only in memory, it is not easy to observe from this single sample.
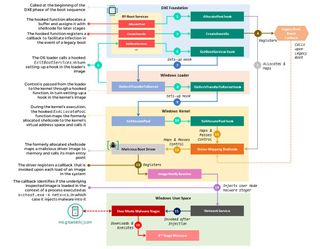
Below is a flowchart explaining how MoonBounce boots and deploys from when your UEFI PC is turned on, through Windows loading, and being a usable but infected PC.
APT41 fingerprint detected
Another important branch of work done by security researchers like Kaspersky is to determine who is behind the malware they discover, what the malware’s goals are, and for what specific targets the malware is primed.
Regarding MoonBounce, Kaspersky seems fairly certain that this malware is the product of APT41, “a malicious actor that has been widely reported to be Chinese-speaking.” In this case, the smoking gun is a “unique certificate” that the FBI has previously reported as signaling the use of APT41-owned infrastructure. APT41 has a history of supply chain attacks, so this is a continuation of a common thread of nefarious APT41 operations.
Security measures
To avoid falling victim to MoonBounce or similar UEFI malware, Kaspersky suggests a number of measures. He recommends that users keep their UEFI firmware updated directly from the manufacturer, verify that BootGuard is enabled if applicable, and enable Trust Platform Modules. Finally, he recommends a security solution that scans for system firmware issues so action can be taken when UEFI malware is detected.


Comments are closed.